In this day and age, crimes on the internet are becoming significantly real, and we all should be worried about the safety and security that the new technology has presented. Earlier you have to be an expert to hack computers, but now anyone can do it. A report says that 60% of the computers are hacked in some way or the other. It could be tough to know whether you are one of them so we decided to throw some useful facts that can assist you in identifying if your privacy is in danger.

01- Anti-Virus Software Disabled On Its Own:
First and foremost, head straight into your computer settings and take a look at your antivirus software status. If your antivirus is enabled and is doing what it is supposed to do first, then things are normal. It is a straight red flag, that your computer is compromised, is when your antivirus status shows disabled or ‘Off” and you never did it yourself. It never happens on its own for sure unless some external force has acted upon it.
It is typically the first thing the hackers do to access your computer. It will grant them an easier entry to navigate around your computer and into your valuable information.
02- Fake Virus Alerts or Install Antivirus Messages:
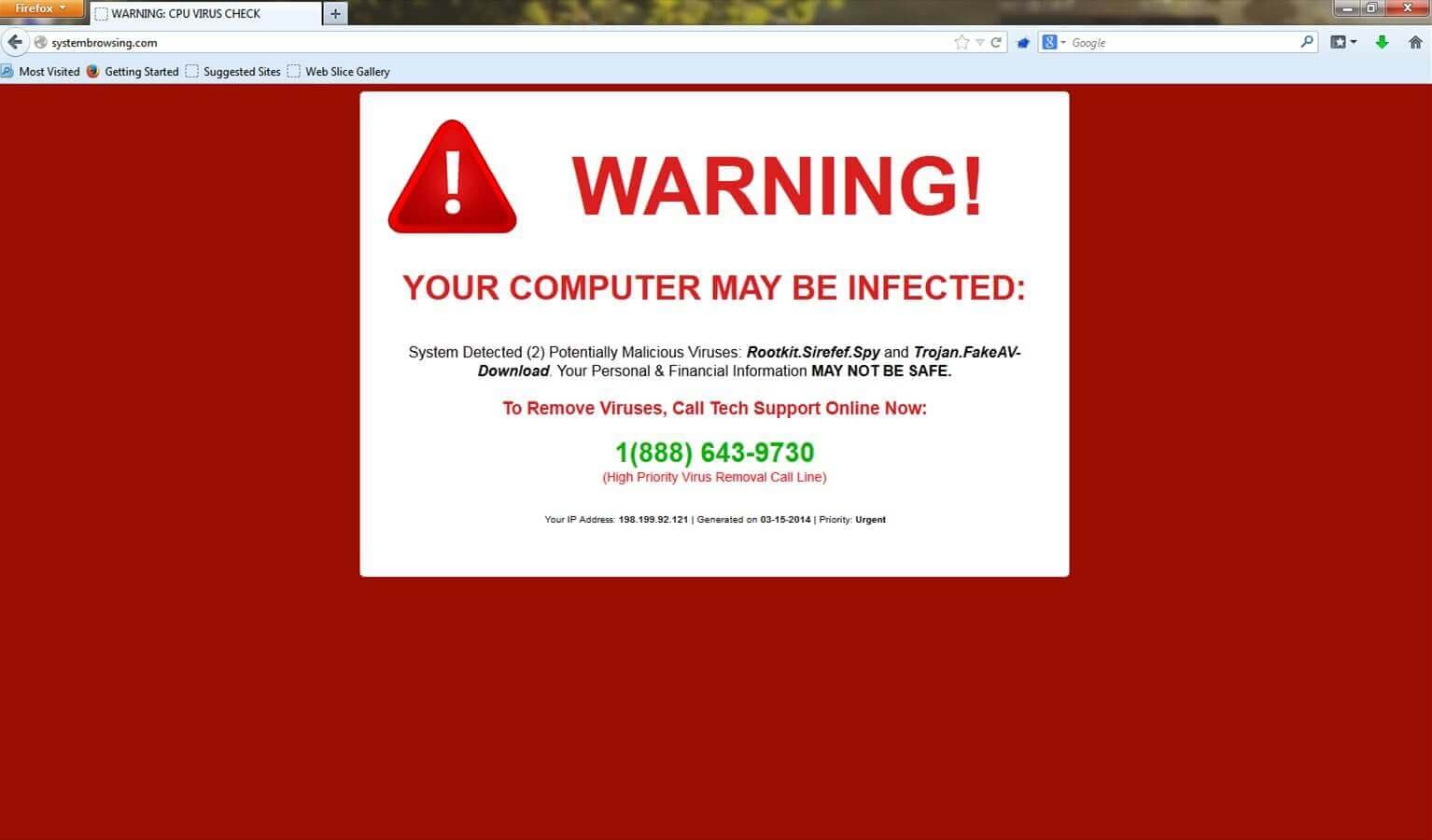
One of the ways a hacker will try to grab you into his clutches is to send you fake virus alerts stating “Your computer is hacked, Click here to fix.” Even some have verbal prompts on them.
The job of your antivirus is to keep anyone from getting into your machine directly meaning if they want to access your information, it will be of your own accord. The fake virus alerts are one the most common ways that the people fall prey to attacks for they click on the message as they are concerned. But instead of being helpful, it, in fact, ends up granting a hacker right of entry to your computer. It is like opening the door to a burglar and handing him your keys by saying “Now I give you permission to access anything anytime you want.” So, ignore the alerts and do not download these fake antivirus software.
03- Replaced Toolbars:
We may have observed that the toolbars or favorites on the web browser get randomly changed or deleted by a software update; It is frustrating if you miss out on un-checking the box to not allow that and you get a brand-new toolbar overwritten on the existing one. If it happens on a bigger scale, you may need to do some investigation.
Usually, when you install software, the web browser resets to default. If this occurs without the knowledge or something is appended to your toolbar or favorites, immediately rush your computer to a specialist who can handle these issues better. If stuff is being added or removed without you physically doing it, then there must be miscreants inside your computer. A hacker is trolling in there, and you are vulnerable to losing your valuable data sooner or later.
Never enter any passwords or log into your net banking if these toolbars appear. It means you are serving your personal information on the hacker’s platter.
04- Phishing Files:
One of the primary reasons why hackers hack into Computer is to steal your files. They usually sneak into your computer’s hard drive which houses all your data. If you experience a ton of files recently taken out or added, then this is probably a hacker’s attack. The only way to safeguard your deleted files is to have a backup. Never open the files which you are not aware of and be sure to remove them as well. Usually, these files are exe files ( Application.exe).
Fig: A fake email example
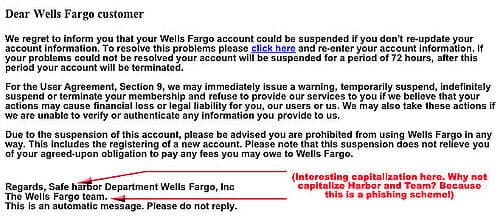
Usually, you download these files through phishing emails which entice you to click a link or download a file or a report. So, beware of such emails and never click on emails that don’t expect or are you not aware. The hackers sometimes disguise their emails by naming your banks, government agencies, famous companies or e-commerce sites, or your social media domains. Be sure to check whether these emails are coming from them by just checking the send email domain name. For example, facebook@sjcyr.com or incometaxdept@incometaxdeptklsu.net. Always make sure the domain address suffixed after ‘@’ are genuine.
05- Numerous Pop-ups:
Who doesn’t hate the irritating pop-ups on his computer screen but it is okay once in a while. But, if they pop up frequently, something could be wrong. The first thing a hacker does typically to sneak in is to disable your antivirus and popup blocking option.
So it is not normal that all of a sudden you start getting a barrage of them. So, don’t forget to check your settings if any suspicious activity occurs without your consent. Apparently, something is fishy with your computer, and it could be compromised.
06- Redirecting Web Searches:
Another red flag is if your web searches start getting redirected to some random websites. Many hackers redirect you to those viruses that demand manual installations.
Often, these hackers try to trap you into clicking on their virus link. The click disables the antivirus and downloads with your consent thus bypassing the antivirus trap. It is a big red flag if you experience frequent redirects to spam websites. It is obviously unsafe and if this is repeatedly occurring, then look into your antivirus settings and check if anything is being modified or the system has been hacked.
07-Passwords are Not Working:
When you log in to your social media accounts or other online accounts and your passwords suddenly fail, then you are in trouble. A familiar tactic in stealing data is to throw the real person out of his accounts by changing the login passwords.
Never use personal details in your passwords. Never use birth dates, children’s names, spouse’s names, anniversaries, anything like that. Create complex passwords by putting uppercases, numerical and special characters. Use longer strings for passwords. The more complicated it is, the better. So just by a rule of thumb change your passwords regularly.
08- Spam Requests to Friends:
If your friends receive social media invites that you didn’t send then something is fishy. It occurs commonly on Facebook, but it means it can be damaging. Nobody is capable of transmitting messages to your friends from your side other than you unless they have your log in details.
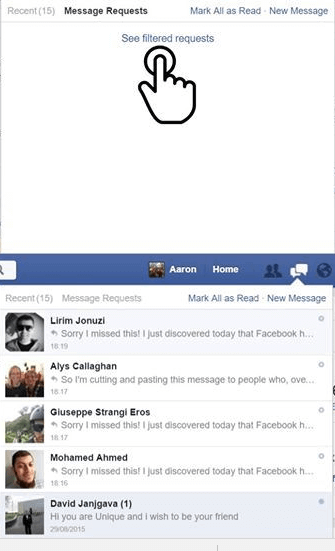
So, maybe you clicked on some ad there or accidentally permitted some app on Facebook. Hackers are cheeky and prey on the gullible, and they are many of them infesting the social media platforms like Facebook and Twitter.
But whatever the motive may be, you should change your passwords and check your settings right away. To be safer from such calamities, if there is a two-step verification process when you are registering for social media accounts you should go for it.
Also, hackers access your account through your SIM cards or mobile phones. So, ascertain that your service provider is responsive to a 2 step verification or some code or one time passwords (OTP) to secure your accounts so that nobody enters and compromises your account. If the hackers break into your phones, they can access all of your accounts.
Don’t forget to report it to the platforms about these issues.
09- Unapproved Installation of Software:
In most computers, no software will download or install unless you permit to do so. Nevertheless, if software starts downloading without your approval, you must stop it immediately. Yes, sometimes computers mess up and inadvertently download the regular updates like a Microsoft. It usually happens without your authorization but stuff does get downloaded from random sources without your permission.
It is certain that there is something wrong with your computer. A lot of this is regular information, but you will be amazed how many hackers, every day, grab the advantage of those who ignore at these fundamentals.
10- An Involuntary Movement of Pointer:
If your arrow moves on its own and your mouse isn’t, it is a definite sign to ascertain that your computer is being hacked. When the mouse is moving involuntary, it means it is making selections. If this happens, then you are in bad luck. It signifies a hacker has ghosted into your computer and has snatched the control from you.
11- Webcam Light Blinks:
It is one of the creepiest signs to know that you are being hacked. Your webcam should have no light unless it is on or you are using it. But if you the light on, it indicates that your webcam is on. If you didn’t start it, then this could mean somebody else is using it.

When you use the webcam, your webcam light usually stays ON, but it will flicker if hackers use it. It means the hacker is establishing a connection to disable the flash from showing off for too long. It sounds creepy as the hacker can scan everything you are doing. To test this, you need to turn off your computer and then turn it back on after 20 minutes. If it is still acting up, it is likely that you are being hacked.
12- Printer is Not Connecting:
If you connect your computer to your printer and it fails to connect, one of the reasons may be that your computer is under attack. If your physical connections look in place, and you still get the error, it means that new connections are being made from your computer to the hacker.
Sometimes the attack can damage the other connections as well like a USB. If the printer shows an error with the word “Interrupt,” it means something or someone is blocking the connection. So you need to check on with your cyber security settings as you are likely being hacked.
13- Ransom Warnings:
Thanks to the Ransomware attack these days, the ransom messages are also a significant threat. These are uncommon, and you have to be naive to fall for it. It is when you receive a pop up stating that your computer is under ransom virus attack and you need to pay in cryptocurrencies to fix it.

Most of the time these warnings are useless, and it can be ignored by just restarting your computer. However, if you reboot your computer and the ransom message is still hanging there, or it locks you out of specific programs on your computer, you may be in deep trouble. Keeping a backup of your data is advisable as you may need to format your computer to get rid of it.
These are the thirteen possible ways how your computer can be hacked. A lot of the hacks are easy to spot, and you obviously know few of them, but then there are people out there who are unsuspecting and naive to these facts. So hopefully, next time you should be more aware of such issues.